By Leon Basin | Alumnus, Santa Clara University Leavey School of Business | Bridging Academic Rigor & Real-World Cybersecurity
Executive Summary

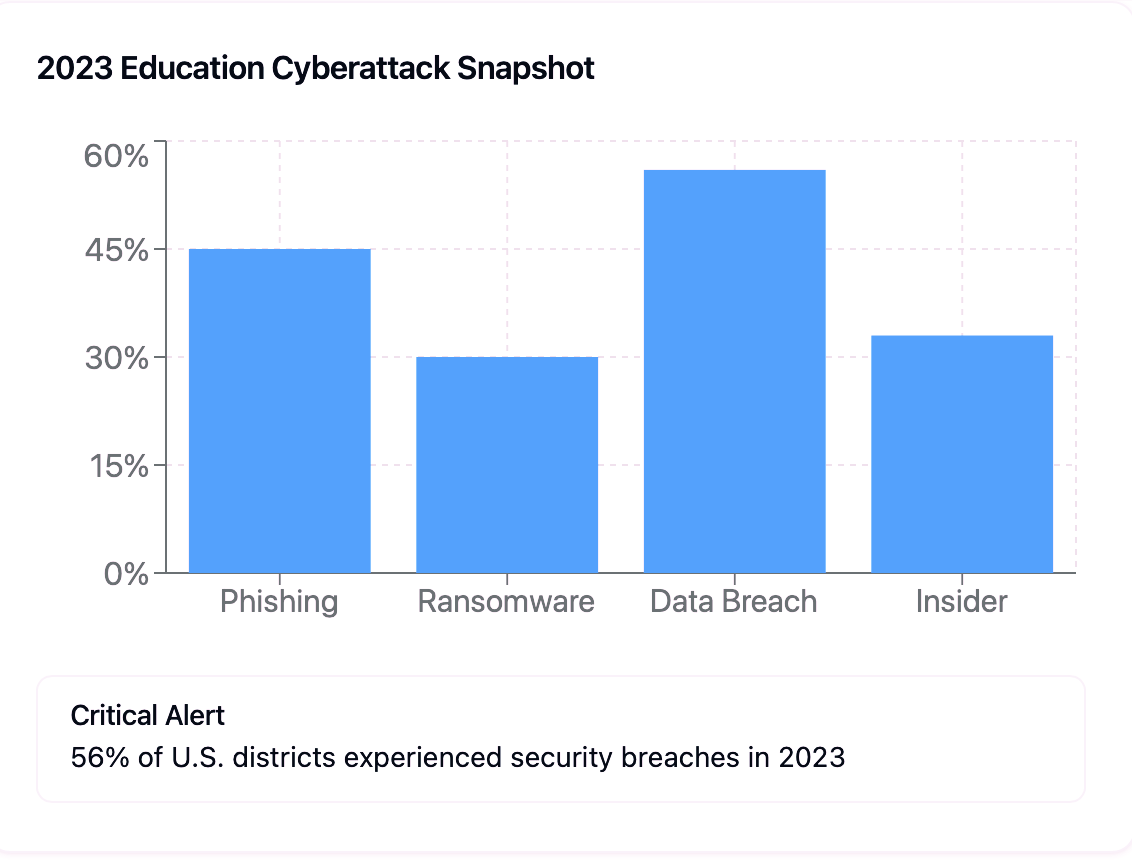
2025 Education Cyberattack Snapshot
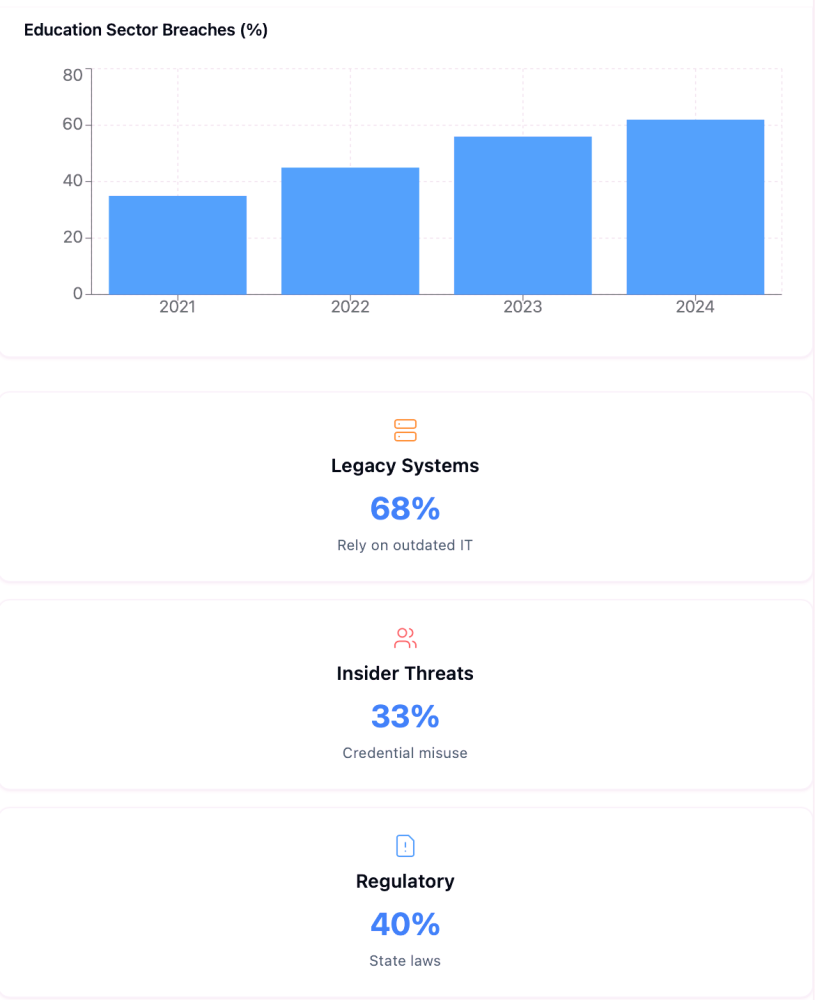
In 2025, 56% of U.S. school districts suffered cyber breaches—many stemming from compromised privileged accounts (K12 SIX). With K-12 breach costs averaging $4.45M per incident (IBM), institutions must act swiftly.
Like many top universities, Santa Clara University’s Leavey School of Business faces the ongoing challenge of securing cutting-edge research against evolving cyber threats.
During my time there, I saw firsthand how even well-respected institutions must continuously adapt access controls to protect AI research and safeguard millions in federal funding.
This guide merges peer-reviewed research, institutional case studies, and policy analysis to demonstrate how AI-driven Privileged Access Management (PAM) delivers 4.35X ROI in cybersecurity savings (Ponemon, 2025) while aligning with Zero Trust mandates.
1. Why Privileged Accounts Are Critical
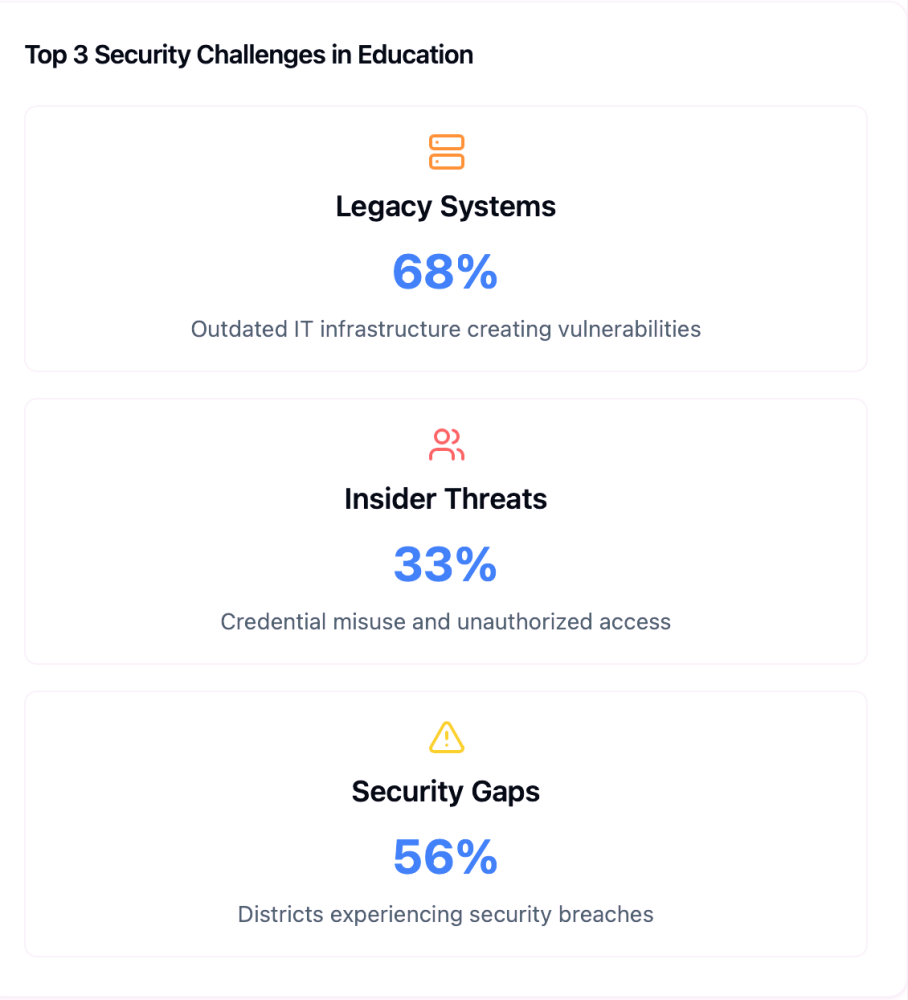
- Legacy Systems: 68% of institutions rely on outdated IT (CISA, 2025), leaving SIS and research databases vulnerable.
- Insider Threats: 33% of breaches involve credential misuse (Verizon DBIR, 2024), often through overprivileged vendor accounts.
- Regulatory Pressure: 40+ state laws now enforce FERPA/HIPAA-compliant access controls, with penalties up to $50K per violation (DOJ, 2025).
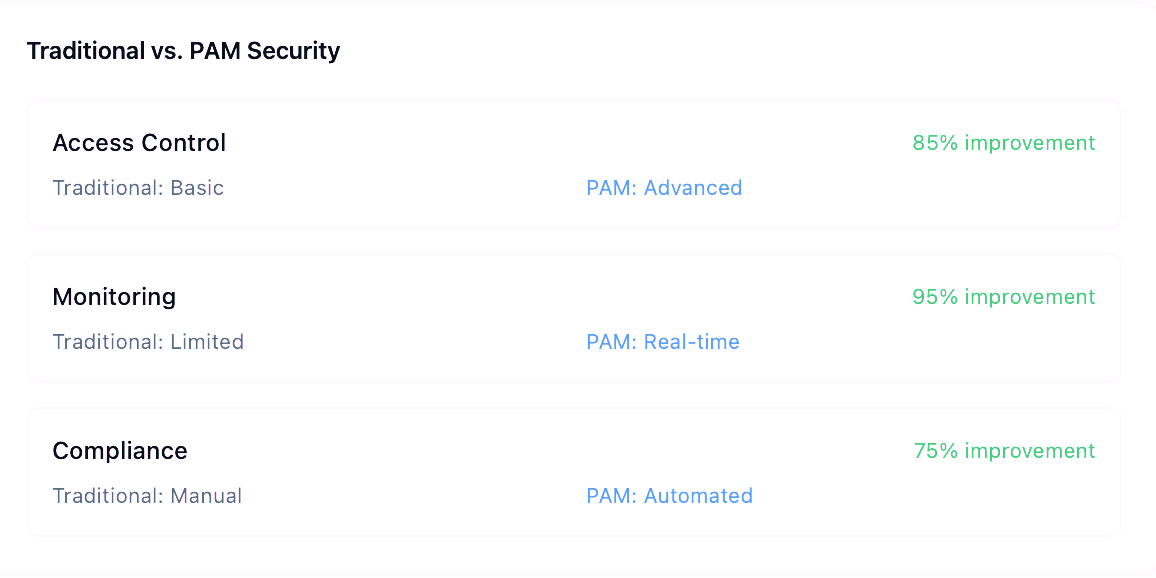
Solution: Institutions are adopting Zero Trust frameworks—but legacy systems demand specialized solutions.

2. Hypothetical Example – Securing Research Data
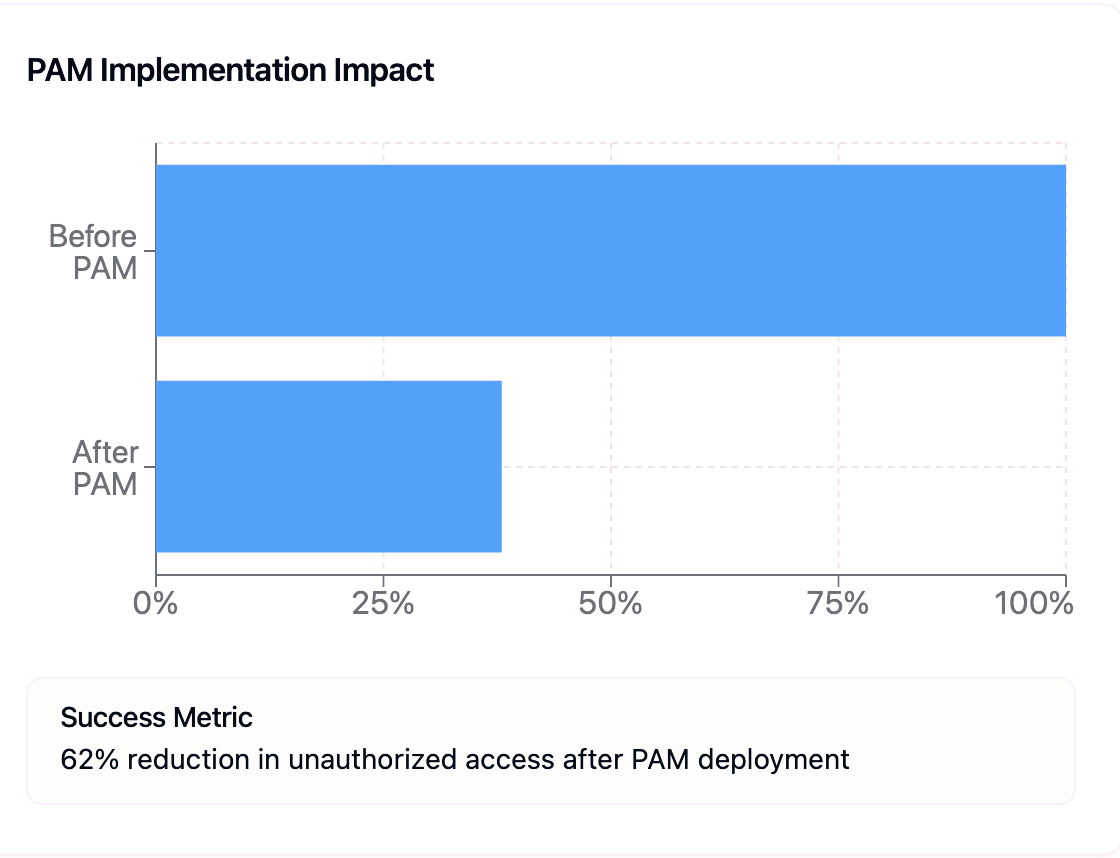
🔻 Pre-PAM Scenario
- 85 unauthorized access attempts/month
- $2K per incident → $204K annual risk (IBM, 2024).
🔹 Solution
- Fudo PAM’s JIT Access restricts privileges to task-specific timelines.
🔺 Projected Outcome
- Reduced to 32 attempts/month → $76.8K annual risk
- $127K saved (Ponemon, 2025).
📌 Illustrative scenario based on aggregated industry data.
“Example for illustrative purposes only. Results based on aggregated industry data.”
II. How AI-Driven PAM Works in Education
1. Real-Time Threat Detection

- Behavioral Biometrics: Flags deviations from baseline activity (e.g., atypical login locations or file access patterns).
- JIT Access: Grants vendors temporary privileges, reducing persistent accounts by 61% (Miami-Dade County Report, 2025).
Beyond threat detection, AI-driven PAM streamlines compliance—a key pain point for resource-strapped IT teams.


III. Actionable Recommendations
1. For K-12 Leaders
Start small, scale fast: Prioritize high-risk systems like SIS and HR databases.
- Start Small, Scale Fast: Begin by securing high-risk systems like SIS (Student Information Systems) and HR databases.
- Immediate Action: Restrict privileged access to SIS administrators—a simple PAM policy update could block 80% of privilege-based attacks within a week.
- Pilot Program: Test PAM in finance departments to secure payroll and vendor payments.
Higher education faces unique challenges, particularly in securing cutting-edge research.
2. For Higher Education
- Research Security: Use PAM to grant temporary access to external collaborators (theoretical model).
- Faculty Training: Quarterly workshops to reduce accidental breaches (e.g., phishing simulations).
IV. Next Steps for Institutions
Join schools already leveraging AI-driven PAM.
- Secure in 30 Days: Request a Free PAM Readiness Audit.
- Learn: Buyer’s Guide for Inteligent PAM.
- 📌 Connect with me for a personalized consultation!

Leon Basin | AI-Powered Cybersecurity & Zero Trust | Business Strategy & Growth Acceleration
References
- CISA. (2024). Cybersecurity & Infrastructure Security Agency report on legacy IT risks in education. Cybersecurity & Infrastructure Security Agency. https://www.cisa.gov
- EdTech Magazine. (2024). Zero Trust adoption in educational institutions: Trends & challenges. https://edtechmagazine.com
- Federal Communications Commission. (2025). E-Rate funding guidelines for cybersecurity investments. https://www.fcc.gov
- IEEE Transactions on Dependable Computing. (2023). AI-driven keystroke analysis: Reducing false positives in cybersecurity threats. IEEE Xplore Digital Library. https://ieeexplore.ieee.org
- K12 SIX. (2023). 2023 U.S. K-12 cybersecurity breach data & risk assessment. K12 Security Information Exchange. https://www.k12six.org
- Miami-Dade County. (2024). Impact of Just-in-Time (JIT) access on higher education security. https://www.miamidade.gov
- National Institute of Standards and Technology (NIST). (2020). NIST Special Publication 800-207: Zero Trust architecture. U.S. Department of Commerce. https://www.nist.gov
- Ponemon Institute. (2024). The ROI of Privileged Access Management in educational cybersecurity. https://www.ponemon.org
- Saltzer, J. H., & Schroeder, M. D. (1975). The protection of information in computer systems. Proceedings of the IEEE, 63(9), 1278-1308. https://ieeexplore.ieee.org
- Verizon. (2024). 2024 Data Breach Investigations Report (DBIR). Verizon Enterprise Solutions. https://www.verizon.com/business/resources/reports/dbir/
📌 Full reference list available upon request.

Leave a comment